AMD Like Intel: Ryzens 5000 With Serious Security Vulnerability
AMD confirms that the new line of processors based on Zen 3 is vulnerable to a Spectre attack. The reason is the optimization mechanism included in the Ryzen 5000 and Epyc processors, among others.
- The latest AMD processors from the Zen 3 generation are vulnerable to Spectre attacks;
- The PSF optimization feature is responsible for this, but disabling it does not result in a significant performance drop.
The Spectre vulnerability, which until now was a characteristic of older Intel and ARM processors, has now also been confirmed on AMD. This is due to the new PSF (Predictive Store Forwarding) feature present in Zen 3 processors. Their optimization mechanism contains a vulnerability through which security measures can be bypassed.
AMD has published a document reporting that the company is aware of the vulnerability in the microarchitecture of the PSF hardware optimization. This is a new feature that appeared in Zen 3 chips, and it aims to speed up their operation by predicting certain actions in the processor's instruction stack. Sometimes this prediction leads to errors through which it is possible to run malicious code and read the contents of memory. For those interested - it is described in more detail in this file.

The most vulnerable is software that uses sandboxes in security processes. Applications that use hardware isolation are not vulnerable. AMD discovered that isolation of addressing protects against this type of attacks. Of course you can always disable the PSF. And it turns out that it's not such a bad idea at all. Although AMD does not recommend it, claiming the threat is low to begin with.
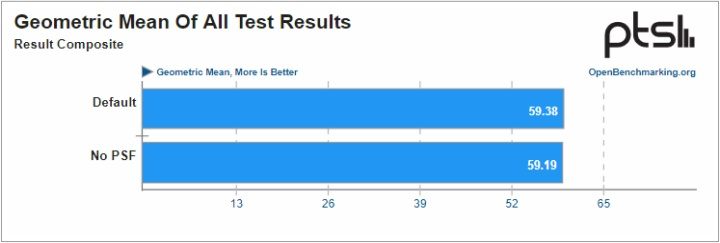
The results of tests performed and published by Phoronix show that the performance drop when PSF is turned off is minimal. Dozens of different benchmarks were performed using various Ryzen 5000 and Epyc 7003 series processors on a Linux platform. The average performance drop was less than one percent and can be assumed irrelevant.
- Just 10 days until Windows 10 support ends. Here’s what you need to know
- “This was not a breach of Discord,” the company clarified, dismissing rumors. Still, reports say that over 2 million “items” were stolen from a third-party vendor
- „Intel was on a mission to kill us” says Jensan Huang. Now, the company will make two microprocessors for NVIDIA
0

Author: Arkadiusz Strzala
His adventure in writing began with his own blog and contributing to one of the early forums (in the olden days of Wireless Application Protocol). An electrical engineer by profession, he has a passion for technology, constructing and, of course, playing computer games. He has been a newsman and writer for Gamepressure since April 2020. He specializes in energy and space tech. However, he does not shy away from more relaxed matters every now and then. He loves watching science-fiction movies and car channels on YouTube. He mainly plays on the PC, although he has modest console experience too. He prefers real-time strategies, FPS and all sorts of simulators.
Latest News
- Huge Marvel Adventures mod now with new superheroes, including Sentry
- Butcher's Summit, an impressive free diselpunk FPS, has been released
- Free FPS on Half Life engine gets big update
- On February 3, gaming history could change forever. Red Dead Redemption 2 one step away from a major achievement
- This is not the RPG you expected. Crimson Desert abandons the key elements of the genre, going for original solutions

