Undetectable Malware on SSDs; Serious Vulnerability Discovered
After CPUs, GPUs, printers, etc. we finally lived to see a security vulnerability in storage drives. As it turns out, modern SSDs allow for undetectable viruses to be installed.
1

It's not just gamers who have the misfortune to find out about the ingenuity of hackers. That's why some researchers are prophylactically looking for vulnerabilities in software and hardware before they are discovered by thieves. After Steam, CPUs, GPUs, printers, etc. researchers have found a way to install undetectable malware directly into SSDs.
The vulnerability discovered by researchers from the Korea University in Seoul (via BleepingComputer.com) is based on the use of so-called over-provisioning (OP) associated with Micron's flex capacity technology. This technology is present in virtually all modern SSDs and, in a nutshell allows for the drive's performance and lifespan to be increased by matching the free, "raw" space to that used by the user.
The former - the de facto empty space - is the aforementioned "over-provisioning", and this part of an SSD is completely inaccessible to the system and programs. Although this doesn't concern - how else - hackers.
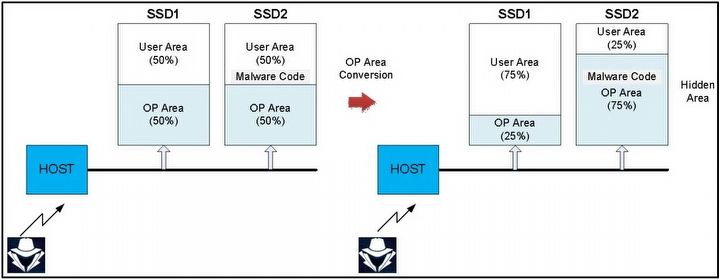
Koreans presented two attack patterns using this vulnerability. The first is simply hiding malware directly in "over-provisioning". This was shown on the example of two drives, both half-used by the user. The malware installs itself on the over-provisioning of the second SSD, on which it expands this "empty" space to 75%, while reducing it to 25% on the first device. As a result, the virus has more space to operate, while the user still sees the same amount of "unused" OP space (i.e. 50%):
"It is assumed that two storage devices SSD1 and SSD2 are connected to a channel in order to simplify the description. Each storage device has 50% OP area. After the hacker stores the malware code in SSD2, they immediately reduce the OP area of SSD1 to 25% and expand the OP area of SSD2 to 75%.
At this time, the malware code is included in the hidden area of SSD2. A hacker who gains access to the SSD can activate the embedded malware code at any time by resizing the OP area. Since normal users maintain 100% user area on the channel, it will not be easy to detect such malicious behavior of hackers."
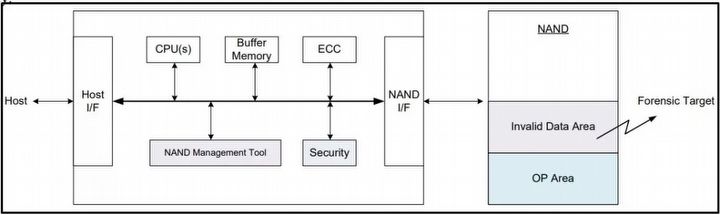
The second pattern uses the invalid data area, which is where the de facto information deleted by the operating system, but physically still present on the SSD (these drives rarely perform such a thorough cleaning) is stored. Again, a hacker can resize the "over-provisioning", which will increase this "buffer" between the OP and the usable space.
Fortunately, so far there have been no reports of hackers carrying out a similar attack. Nevertheless, Korean researchers recommend manufacturers to implement options that would allow for monitoring of OP, better protection of SSD managers against unauthorized actions in this space, and a deletion algorithm that would "physically" delete invalid data without reducing performance in real time.
1

Author: Jacob Blazewicz
Graduated with a master's degree in Polish Studies from the University of Warsaw with a thesis dedicated to this very subject. Started his adventure with gamepressure.com in 2015, writing in the Newsroom and later also in the film and technology sections (also contributed to the Encyclopedia). Interested in video games (and not only video games) for years. He began with platform games and, to this day, remains a big fan of them (including Metroidvania). Also shows interest in card games (including paper), fighting games, soulslikes, and basically everything about games as such. Marvels at pixelated characters from games dating back to the time of the Game Boy (if not older).
Latest News
- Huge Marvel Adventures mod now with new superheroes, including Sentry
- Butcher's Summit, an impressive free diselpunk FPS, has been released
- Free FPS on Half Life engine gets big update
- On February 3, gaming history could change forever. Red Dead Redemption 2 one step away from a major achievement
- This is not the RPG you expected. Crimson Desert abandons the key elements of the genre, going for original solutions