AMD, Nvidia and Intel Drivers Susceptible to Dangerous Attacks
Eclypsium has been involved in online threat research for years. Their latest report, Screwed Drivers, shows something disturbing. According to its content, more than 40 drivers from at least 20 leading manufacturers are vulnerable to attacks.

The report published by Eclypsium revealed something disturbing. Drivers from almost 20 leading manufacturers, contain security gaps. They can give attackers full access to hardware that is not usually available even to administrators of a given environment.
Analysis has shown that the problem affects more than 40 of the latest drivers from nearly 20 leading manufacturers. The list includes, among others:
- ASRock
- ASUSTeK Computer
- ATI Technologies (AMD)
- Biostar
- EVGA
- Getac
- GIGABYTE
- Huawei
- Insyde
- Intel
- Micro-Star International (MSI)
- NVIDIA
- Phoenix Tchnologies
- Realtek Semiconductor
- SuperMicro
- Toshiba
Among them was every BIOS supplier and hardware manufacturer. What's worst about the whole thing is that all the vulnerable drivers have been certified by Microsoft, as if there was no problem with them.
Ordinary users have Ring 3 privileges. Malware can grant Ring 0 privileges to the attacker (and even to the user himself). This is the most privileged form that allows full access to the operating system, hardware interface and firmware.
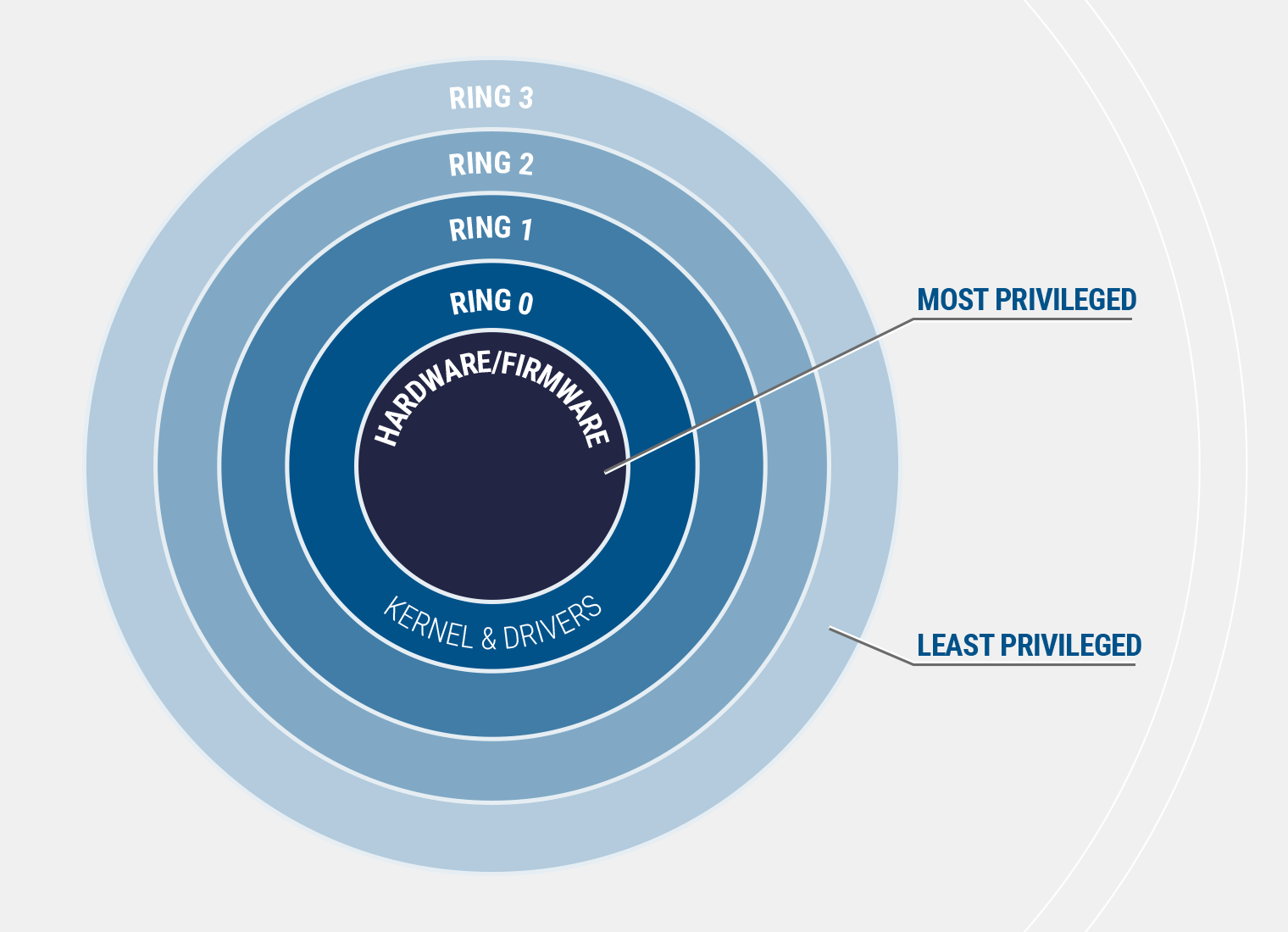
Currently, we do not have any mechanism at our disposal that would allow us to effectively protect our computers. However, if you are extremely worried about your equipment, we have a few tips for you:
- Be careful what you install on your computer - especially drivers.
- Regularly scan your system for potential threats.
- Update the drivers to the latest version.
- Use Windows Defender Application Control (WDAC) to restrict access to certain functions.
Finally, it is worth noting that the report does not reveal all vendors whose software may have some gaps. Even if you do not own anything from the companies listed above, it is also worth following at least some of the above advice.
- Screwed Drivers - full report from Eclypsium
- Detailed description of risks in the form of presentation
- Malware Called „Agent Smith” Infects Over 25 Million Android Devices
- Is Fan Control dangerous? What the Vigrof.a „virus” alert really means
- Windows 10 will lose access to security updates in 29 days. Microsoft didn't change its mind until the very end
- A critical security flaw in Unity Engine was discovered after 8 years. It puts players at risk, and now all games need an urgent patch
0
Latest News
- Elite Mod lets you play the Tau faction in Warhammer 40K: Dawn of War 2
- Huge Marvel Adventures mod now with new superheroes, including Sentry
- Butcher's Summit, an impressive free diselpunk FPS, has been released
- Free FPS on Half Life engine gets big update
- On February 3, gaming history could change forever. Red Dead Redemption 2 one step away from a major achievement

